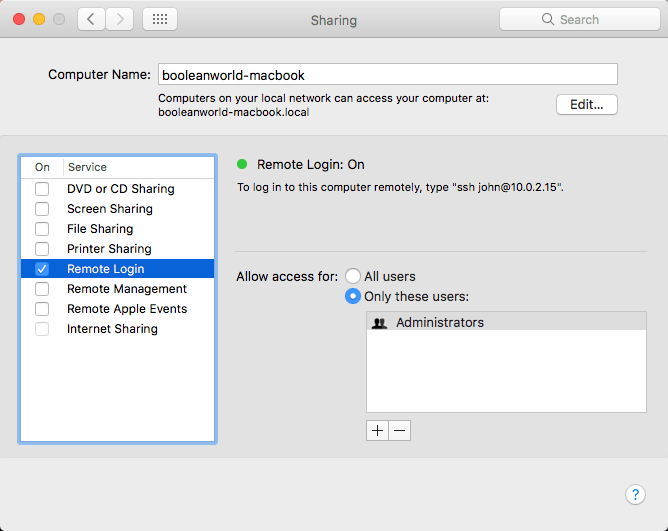
The easiest method to set up SSH connection to is by downloading and running an automated installer. The installer will add SSH configuration entries to /.ssh/configand create a private SSH key file inside /.ssh. This method works best if you have only one account. Download and save the automatic installer script customized for your account. To start SSH on macOS go to System Preferences Sharing Remote Login. You can also do it from the command line with sudo systemsetup -setremotelogin on. To turn it off from the command line use sudo systemsetup -setremotelogin off. To check if remote login is enabled/disabled use sudo systemsetup. This is available even on a fresh install of macOS. The command is: xcode-select -install According to the man page: Opens a user interface dialog to request automatic installation of the command line developer tools. It seems to have been available since Xcode 3.0 was around (OS X 10.5).
If you are running Linux or a macOS operating system you can access the cluster using the native Secure Shell (SSH) client, you will need to set up SSH tunneling as described below.
Option 1: Automated Configuration
The easiest method to set up SSH connection to is by downloading and running an automated installer. The installer will add SSH configuration entries to ~/.ssh/config and create a private SSH key file inside ~/.ssh. This method works best if you have only one account.
- Download and save the automatic installer script customized for your account:
- Execute this script in a terminal (you may need to adjust the command according to your download location and the downloaded file name):
- Clean up for security:
Option 2: Manual Configuration
Alternatively, if you do not want a script to modify your SSH configuration, you can proceed with manual installation instructions below.
Direct SSH Connection
- Download and save the SSH access key for Linux/macOS to the folder ~/Downloads/ on your computer
* Sign In to see the download link. - Create the directory ~/.ssh, unless it already exists and move the private SSH key into permanent storage in ~/.ssh:If you saved your key in a location other than ~/Downloads/, insert the correct path.
* Sign In to see the value of <user> for your account. - Add the following lines to file ~/.ssh/config (if you do not have this file, simply create one):Note: if you have multiple accounts on the Intel DevCloud, you can change the hostname devcloud to any other identifier to differentiate between your accounts. This is the hostname that you will use in the ssh and scp commands.
* Sign In to see the value of <user> for your account. - Set the correct restrictive permissions on it and on the SSH client config file. To do this, run the following commands in a terminal:* Sign In to see the value of <user> for your account.
Direct SSH Connection
The following SSH settings are required for Visual Studio Code* remote access.
* Sign In to see the value of <user> for your account.If you Are Behind an SSH Proxy
In the interest of security, some business networks require that all outgoing connections are established via a corporate proxy. If you followed the instructions above but are getting the error 'Connection timed out', you are likely on such a business network. To comply with the security rules of your company, modify ~/.ssh/config as below:
Here, <proxy_name> and <port> are, respectively, the hostname and port of the corporate proxy. It is usually provided to you by your IT department.
Connection
After the preparation steps above, you should be able to log in to your login node in the Intel® DevCloud without a password.
Macos Install Sshuttle
Upon the first login, you will be asked to add the host to the list of known hosts. Answer 'yes':
Macos Ssh Key
Next time you log in, you will only need to type ssh devcloud to log in:
Transferring Files

Once your connection is set up, you can copy local files to your login node like this:
And you can copy files from your login node back to your home computer like this:
Introduction
Setting up SSH based security to access your server is a much more effective way than the use of a manual root password. Cracking the security system of a node depending on SSH keys is nearly impossible since it secures your node in a more sophisticated way by the use of encoded keys.
Why is a password-based authentication vulnerable?
A server can authenticate & grant access to the users with different access methods. The most basic of these is a password-based authentication, which is easy to use but isn’t the most secure.
Modern processing power combined with automated scripts make brute forcing a password-protected account very possible since passwords generally are not complex. SSH keys prove to be a reliable and secure alternative.
What are SSH Keys?
SSH key pairs are two cryptographically secure keys that can be used to authenticate a client to an SSH server. Each key pair consists of a public key and a private key.
The private key is retained by the client on his local machine and should be kept absolutely secret. Any compromise of the private key will allow the attacker to log into servers that are configured with the associated public key without additional authentication. As an additional precaution, the key can be encrypted on disk with a passphrase.
The public key is uploaded onto the remote server that you want to be able to log into with SSH.
When a client attempts to authenticate using SSH keys, the server can test the client on whether they are in possession of the private key. If the key-pair matches then a shell session is spawned or the requested command is executed.
How do SSH keys work
- A key pair will be generated on your local PC.
- Generating a key pair provides you with two long string of characters: a public and a private key.
- The public key will be added to your node.
- The corresponding private key pair will be saved on your local PC.
- Every time you access your node, the SSH system will look up for the private key pair of the public key added to it. The system will unlock only when the two keys match.
- You can also disable the root password after the SSH keys are set up.
Make sure that you add the public key to the servers and the private key is saved in a secure location on your PC.
Setup SSH keys – macOS
The following outlines the process of setting up key-based SSH login on Mac OS X and Mac OS X Server. To set up key-based SSH, you must generate the keys the two computers will use to establish and validate the identity of each other.
This doesn’t authorize all users of the computer to have SSH access. Keys must be generated for each user account.
Step 1 – Verification of .ssh directory
Verify that an .ssh folder exists in your home folder by entering the command-
If .ssh is listed in the output, move to next step.
If .ssh is not listed in the output, run
mkdir ~/.ssh
Change directories in the shell to the hidden .ssh directory by entering the following command:
Step 2 – Create the RSA Key Pair
Generate the public and private keys by entering the following command:
ssh-keygen -b 1024 -t rsa -f id_rsa
(The -b flag sets the length of the keys to 1,024-bits, -t indicates to use the RSA hashing algorithm, -f sets the file name as id_rsa.)
The above command will follow up with some confirmation messages
[root@e2e ~]# ssh-keygen -b 1024 -t rsa -f id_rsa
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
press Enter to set the passprase to null
Two files will be generated after this step.
- id_rsa (Private Key)
- id_rsa.pub (public key)
Note: Keys are equivalent to passwords so you should keep them private and protected.DO NOT SHARE YOUR PRIVATE KEY (id_rsa)
Prior to scp/ssh we have to add the identity to the user for whom we generated the key, by running
Step 3 – Copy the Public Key to your node
Now you can copy and add your public key id_rsa.pub file, to set up SSH on your node under MyAccount.
You can usually get this key by copying the results of:
Paste the results generated from id_rsa.pub to the SSH section under MyAccount.
You may add multiple SSH keys & can provide a label to each SSH key for easy identification & management purpose.
Macos Install Ssh Client
Copy the public key directly to a server (Alternate Approach)
The commandssh-copy-id can be used to install an authorized key on the server.
If you don’t have SSH access to the server then it will require a root password which is shared with you in the email.
Once the key has been authorized for SSH, it grants access to the server without a password.
Use a command like the following to copy SSH key:
Enter the following command to copy your public key to your Node:
This will copy your public key to the authorized_keys file on your server.
Make sure to replace xxx.xx.xx.xx with your actual Ip address and replace user with your actual username in the above command.
Once you enter the ssh-copy-id command, you will see information similar to this:
Only the public key is copied to the server. The private key should never be copied to a machine.
Modifying permissions
For an additional layer of security, modify the file permissions.
Directory .ssh should have 700 permissions and authorized_keys file should have 400 or 600 permissions. To change the permissions, use the following commands:
Now log into the remote server using ssh or scp/sftp:
Was this article helpful?
Related Articles
