I finally found a basic config that does not require any of that. Here is what I have used to access proxy autocomplete google places requests through local host on an installation of Apache including ssl support ( version 2.2 for windows ). Edit the apache file httpd.conf. Turn on the required modules. LoadModule proxymodule modules/modproxy.so LoadModule proxyconnectmodule modules/modproxyconnect.so LoadModule proxyhttpmodule modules/modproxyhttp.so LoadModule ssl.
Here is what I have used to access proxy autocomplete google places requests through local host on an installation of Apache including ssl support (version 2.2 for windows). Edit the apache file httpd.conf. Ports 80 (http) and 443 (https) have been forwarded from your external ip to an internal server at 10.1.1.2 which will handle the reverse proxy and SSL/TLS work using letsencrypt You have other application web servers listening on port 80 on your internal LAN at 10.1.1.11 and 10.1.1.12 but these are not accessible from outside your network. Apr 27, 2017 Hi How can I verify that Endpoint clients and agents (configuration according to hxxp://support.eset.com/kb5950/#Policy2useHttpProxy) are using my new Apache HTTP Proxy?

Scenario
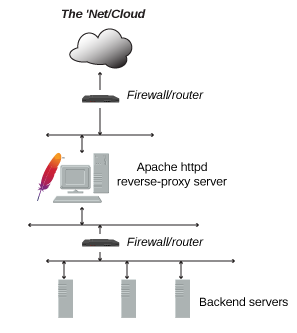

You have a single incoming IP address and want to run multiple web servers for multiple sites behind this IP address on your local network. The best way to do this is using a reverse proxy server For example:

- Your External IP is: 8.8.8.8 with and internal LAN of 10.1.1.X
- Ports 80 (http) and 443 (https) have been forwarded from your external ip to an internal server at 10.1.1.2 which will handle the reverse proxy and SSL/TLS work using letsencrypt
- You have other application web servers listening on port 80 on your internal LAN at 10.1.1.11 and 10.1.1.12 but these are not accessible from outside your network.
- You have subdomain11.yourdomain.com and subdomain12.yourdomain.com both pointed to 8.8.8.8 and you want visitors to them to see the application servers at 10.1.1.11 and 10.1.1.12 respectively.
- You want to provide secure https access to both subdomains but don’t want to configure this on each of the three servers separately.
This guide is based on using Apache2 on Ubuntu 16.04, some commands may differ slightly between different flavours of Linux but the core configuration for Apache2 should work on any distribution.
Instructions (Run All on the Reverse Proxy server – for this example it is 10.1.1.2)
Apache Http To Https Proxy List
- Set up Apache
On the reverse proxy server, install apache web server and enabled the required modules by executing the lines below in terminal - Set up vhost files for each subdomain as per the examples below – this is the key to the super easy reverse proxy config that will support automatic use of letsencrypt and forward incoming traffic to and from each of the application servers from the single incoming IP.
File: /etc/apache2/sites-enabled/subdomain11.confOk so what is going on in this file?
ServerName – tells apache to use the config file when a visitor arrives at your IP address using the domain specified.
DocumentRoot – is the local directory on the ReverseProxy server which will be used to authenticate the server using lets encrypt in the next step
ProxyPass /.well-known ! – tells apache not to forward traffic for the sub directory subdomain11.yourdomain.com/.well-known to the application server. This directory is used by letsencrypt to authenticate your server for SSL so we want to keep that heading to the local directory on the reverse proxy server.
ProxyPass / http:/10.1.1.11:80/ and ProxyPassReverse / http://10.1.1.11:80/ tells apache to forward all other traffic for this domain to the server 10.1.1.11 on port 80Once created you can run the command:
Then browse to http://subdomain11.yourdomain.com and you should see the content hosted on the application server at 10.1.1.11. Once this is working you can create the virtualhost file for your other domain as per below:
File: /etc/apache2/sites-enabled/subdomain12.conf
- This is all good and well but we do not yet have secure https access to these domains. To set this up we are going to use LetsEncrypt which is a great free service for obtaining https certificates for web servers. Install CertBot by following the instructions at their page. For Apache on Ubuntu 16.04 the command is as simple as running the command:
- Once certbot is installed we should be able to run it as per the instructions for your operating system. For Ubuntu 16.04 it is:
Which will take you through a wizard to automatically install the certificates to enable https access. Once complete you should be able to visit https://subdomain11.yourdomain.com and https://subdomain12.yourdomain.com. If you encounter any issues you may want to restart Apache one more time:
Considerations
Apache Http To Https Proxy
One note is that while you will be providing secure connections to visitors from the public internet the traffic between your reverse proxy server and the application servers will not be encrypted. You will need to ensure that the private LAN (in the example 10.1.1.X) is secure from monitoring or MITM attacks (eg. this is a fully private LAN behind a firewall and without any publicly accessible WiFi or Ethernet connections.)
Sources and Thanks
This guide was assembled after a fair session of google-fu. Big thanks to the posts and guides below which have all been drawn upon to create this single guide.
Apache Reverse Proxy
By far the more straightforward tuto i found on the internet.
great many thanks to you !
To make it work, i had to correct the vhost generated by certbot (switching http to https and 80 to 443 and adding a line “SSLProxyEngine”).
I also followed used Mark’s suggestions.
Environment Variables
In addition to the configuration directives that control the behaviour of mod_proxy, there are a number of environment variables that control the HTTP protocol provider. Environment variables below that don't specify specific values are enabled when set to any value.
- proxy-sendextracrlf
- Causes proxy to send an extra CR-LF newline on the end of a request. This is a workaround for a bug in some browsers.
- force-proxy-request-1.0
- Forces the proxy to send requests to the backend as HTTP/1.0 and disables HTTP/1.1 features.
- proxy-nokeepalive
- Forces the proxy to close the backend connection after each request.
- proxy-chain-auth
- If the proxy requires authentication, it will read and consume the proxy authentication credentials sent by the client. With proxy-chain-auth it will also forward the credentials to the next proxy in the chain. This may be necessary if you have a chain of proxies that share authentication information. Security Warning: Do not set this unless you know you need it, as it forwards sensitive information!
- proxy-sendcl
- HTTP/1.0 required all HTTP requests that include a body (e.g. POST requests) to include a Content-Length header. This environment variable forces the Apache proxy to send this header to the backend server, regardless of what the Client sent to the proxy. It ensures compatibility when proxying for an HTTP/1.0 or unknown backend. However, it may require the entire request to be buffered by the proxy, so it becomes very inefficient for large requests.
- proxy-sendchunks or proxy-sendchunked
- This is the opposite of proxy-sendcl. It allows request bodies to be sent to the backend using chunked transfer encoding. This allows the request to be efficiently streamed, but requires that the backend server supports HTTP/1.1.
- proxy-interim-response
- This variable takes values
RFC(the default) orSuppress. Earlier httpd versions would suppress HTTP interim (1xx) responses sent from the backend. This is technically a violation of the HTTP protocol. In practice, if a backend sends an interim response, it may itself be extending the protocol in a manner we know nothing about, or just broken. So this is now configurable: setproxy-interim-response RFCto be fully protocol compliant, orproxy-interim-response Suppressto suppress interim responses. - proxy-initial-not-pooled
- If this variable is set, no pooled connection will be reused if the client request is the initial request on the frontend connection. This avoids the 'proxy: error reading status line from remote server' error message caused by the race condition that the backend server closed the pooled connection after the connection check by the proxy and before data sent by the proxy reached the backend. It has to be kept in mind that setting this variable downgrades performance, especially with HTTP/1.0 clients.
