Cisco VPN error 412 windows 8 - Just Published 2020 Update A device that operates inside the provider's core. Letter a remote-access VPN uses public infrastructure. Armed with the tools we need, let's follow the steps necessary to install and configure the VPN client on Windows 10. If a previous version of Cisco's VPN Client is currently installed on the. Hello, From the link that you have, you will need to port-forward all those Port Nos. This guide should give you an idea on how to do port forwarding. Follow johnwill's advice first and see if VPN is not being blocked by your ISP.
Building configuration...
Current configuration : 8568 bytes
!
version 12.3
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
service sequence-numbers
!
hostname Router
!
boot-start-marker
boot-end-marker
!
logging buffered 51200 debugging
logging console critical
enable secret 5 $1$LR.f$pB8.ZdKhW3GXtV8S4gj3J.
!
username James privilege 15 secret 5 $1$lURO$tewOxEtKEAqZxNz7Zdbd4.
clock timezone London 0
clock summer-time London date Mar 30 2003 1:00 Oct 26 2003 2:00
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default if-authenticated local
aaa authorization network default local
aaa session-id common
ip subnet-zero
no ip source-route
!
!
ip cef
ip inspect name DEFAULT100 cuseeme
ip inspect name DEFAULT100 ftp
ip inspect name DEFAULT100 h323
ip inspect name DEFAULT100 icmp
ip inspect name DEFAULT100 rcmd
ip inspect name DEFAULT100 realaudio
ip inspect name DEFAULT100 rtsp
ip inspect name DEFAULT100 esmtp
ip inspect name DEFAULT100 sqlnet
ip inspect name DEFAULT100 streamworks
ip inspect name DEFAULT100 tftp
ip inspect name DEFAULT100 tcp
ip inspect name DEFAULT100 udp
ip inspect name DEFAULT100 vdolive
ip tcp synwait-time 10
no ip bootp server
ip domain name XXX
ip name-server 158.152.1.58
ip name-server 158.152.1.43
ip ssh time-out 60
ip ssh authentication-retries 2
no ftp-server write-enable
!
!
!
!
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
!
crypto isakmp policy 2
hash md5
authentication pre-share
group 2
crypto isakmp key pwd address 82.0.98.178
!
crypto isakmp client configuration group groupname
key key
dns 158.152.1.58 158.152.1.43
wins xxx.xxx.xxx.200
domain XXX
pool SDM_POOL_1
include-local-lan
max-users 1
max-logins 3
!
!
crypto ipsec transform-set TransformSet1 esp-3des esp-sha-hmac
!
crypto ipsec profile IPSecProfile1
set transform-set TransformSet1
!
!
crypto dynamic-map SDM_DYNMAP_1 1
set transform-set TransformSet1
reverse-route
!
!
crypto map SDM_CMAP_1 client authentication list default
crypto map SDM_CMAP_1 isakmp authorization list default
crypto map SDM_CMAP_1 client configuration address respond
crypto map SDM_CMAP_1 65535 ipsec-isakmp dynamic SDM_DYNMAP_1
!
bridge irb
!
!
interface Null0
no ip unreachables
!
interface ATM0
no ip address
no ip redirects
no ip unreachables
no ip proxy-arp
ip route-cache flow
no atm ilmi-keepalive
dsl operating-mode auto
!
interface ATM0.1 point-to-point
description $ES_WAN$$FW_OUTSIDE$
no ip redirects
no ip unreachables
no ip proxy-arp
pvc 0/38
encapsulation aal5mux ppp dialer
dialer pool-member 1
!
!
interface FastEthernet0
no ip address
no cdp enable
!
interface FastEthernet1
no ip address
no cdp enable
!
interface FastEthernet2
no ip address
no cdp enable
!
interface FastEthernet3
no ip address
no cdp enable
!
interface Dot11Radio0
no ip address
!
ssid SSIDname
authentication open
!
speed basic-1.0 2.0 5.5 6.0 9.0 11.0
channel 2462
no cdp enable
bridge-group 1
bridge-group 1 spanning-disabled
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-HWIC 4ESW$$FW_INSIDE$
no ip address
bridge-group 1
!
interface Dialer0
description $FW_OUTSIDE$
ip address 80.177.223.54 255.0.0.0
ip access-group 101 in
no ip redirects
no ip unreachables
no ip proxy-arp
ip inspect DEFAULT100 out
ip nat outside
ip virtual-reassembly
encapsulation ppp
ip route-cache flow
dialer pool 1
dialer-group 1
no cdp enable
ppp authentication chap callin
ppp chap hostname pigot...@lon1-aj1e.demonadsl.co.uk
ppp chap password 7 05082E1D2042405A0A
!
interface BVI1
description $ES_LAN$$FW_INSIDE$
ip address xxx.xxx.xxx.100 255.255.255.0
ip access-group 100 in
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly
ip route-cache flow
ip tcp adjust-mss 1452
crypto map SDM_CMAP_1
!
ip local pool SDM_POOL_1 xxx.xxx.xxx.50 xxx.xxx.xxx.55
ip classless
ip route 0.0.0.0 0.0.0.0 Dialer0
!
ip http server
ip http access-class 2
ip http authentication local
ip http secure-server
ip http timeout-policy idle 600 life 86400 requests 10000
ip nat inside source route-map SDM_RMAP_1 interface Dialer0 overload
!
logging trap debugging
logging xxx.xxx.xxx.100
logging 80.177.223.54
access-list 1 remark INSIDE_IF=BVI1
access-list 1 remark SDM_ACL Category=2
access-list 1 permit xxx.xxx.xxx.0 0.0.0.255
access-list 2 remark HTTP Access-class list
access-list 2 remark SDM_ACL Category=1
access-list 2 permit xxx.xxx.xxx.0 0.0.0.255
access-list 2 deny any
access-list 100 remark auto generated by Cisco SDM Express firewall
configuration
access-list 100 remark SDM_ACL Category=1
access-list 100 permit ip host xxx.xxx.xxx.50 any
access-list 100 permit ip host xxx.xxx.xxx.51 any
access-list 100 permit ip host xxx.xxx.xxx.52 any
access-list 100 permit ip host xxx.xxx.xxx.53 any
access-list 100 permit ip host xxx.xxx.xxx.54 any
access-list 100 permit ip host xxx.xxx.xxx.55 any
access-list 100 permit udp any host xxx.xxx.xxx.100 eq non500-isakmp
access-list 100 permit udp any host xxx.xxx.xxx.100 eq isakmp
access-list 100 permit esp any host xxx.xxx.xxx.100
access-list 100 permit ahp any host xxx.xxx.xxx.100
access-list 100 deny ip 80.0.0.0 0.255.255.255 any
access-list 100 deny ip host 255.255.255.255 any
access-list 100 deny ip 127.0.0.0 0.255.255.255 any
access-list 100 permit ip any any
access-list 101 remark auto generated by Cisco SDM Express firewall
configuration
access-list 101 remark SDM_ACL Category=1
access-list 101 permit ip host xxx.xxx.xxx.50 any
access-list 101 permit ip host xxx.xxx.xxx.51 any
access-list 101 permit ip host xxx.xxx.xxx.52 any
access-list 101 permit ip host xxx.xxx.xxx.53 any
access-list 101 permit ip host xxx.xxx.xxx.54 any
access-list 101 permit ip host xxx.xxx.xxx.55 any
access-list 101 permit udp any host 80.177.223.54 eq non500-isakmp
access-list 101 permit udp any host 80.177.223.54 eq isakmp
access-list 101 permit esp any host 80.177.223.54
access-list 101 permit ahp any host 80.177.223.54
access-list 101 permit udp host 82.0.98.178 host 80.177.223.54 eq
non500-isakmp
access-list 101 permit udp host 82.0.98.178 host 80.177.223.54 eq
isakmp
access-list 101 permit esp host 82.0.98.178 host 80.177.223.54
access-list 101 permit ahp host 82.0.98.178 host 80.177.223.54
access-list 101 permit udp host 158.152.1.43 eq domain host
80.177.223.54
access-list 101 permit udp host 158.152.1.58 eq domain host
80.177.223.54
access-list 101 deny ip xxx.xxx.xxx.0 0.0.0.255 any
access-list 101 permit icmp any host 80.177.223.54 echo-reply
access-list 101 permit icmp any host 80.177.223.54 time-exceeded
access-list 101 permit icmp any host 80.177.223.54 unreachable
access-list 101 deny ip 10.0.0.0 0.255.255.255 any
access-list 101 deny ip 172.16.0.0 0.15.255.255 any
access-list 101 deny ip 192.168.0.0 0.0.255.255 any
access-list 101 deny ip 127.0.0.0 0.255.255.255 any
access-list 101 deny ip host 255.255.255.255 any
access-list 101 deny ip host 0.0.0.0 any
access-list 101 deny ip any any
access-list 101 remark IPSec Rule
access-list 101 permit ip xxx.xxx.xxx.0 0.0.0.255 xxx.xxx.xxx.0
0.0.0.255
access-list 103 remark SDM_ACL Category=2
access-list 103 deny ip any host xxx.xxx.xxx.50
access-list 103 deny ip any host xxx.xxx.xxx.51
access-list 103 deny ip any host xxx.xxx.xxx.52
access-list 103 deny ip any host xxx.xxx.xxx.53
access-list 103 deny ip any host xxx.xxx.xxx.54
access-list 103 deny ip any host xxx.xxx.xxx.55
access-list 103 permit ip xxx.xxx.xxx.0 0.0.0.255 any
access-list 105 remark VTY Access-class list
access-list 105 remark SDM_ACL Category=1
access-list 105 permit ip xxx.xxx.xxx.0 0.0.0.255 any
access-list 105 deny ip any any
access-list 700 permit 0001.e694.aa0a 0000.0000.0000
access-list 700 deny 0000.0000.0000 ffff.ffff.ffff
dialer-list 1 protocol ip permit
no cdp run
route-map SDM_RMAP_1 permit 1
match ip address 103
!
!
control-plane
!
bridge 1 protocol ieee
bridge 1 route ip
banner login ^CAuthorized access only!
Disconnect IMMEDIATELY if you are not an authorized user!^C
!
line con 0
no modem enable
transport preferred all
transport output telnet
line aux 0
transport preferred all
transport output telnet
line vty 0 4
access-class 105 in
transport preferred all
transport input telnet ssh
transport output all
!
scheduler max-task-time 5000
scheduler allocate 4000 1000
scheduler interval 500
ntp server 130.88.203.12 prefer
end
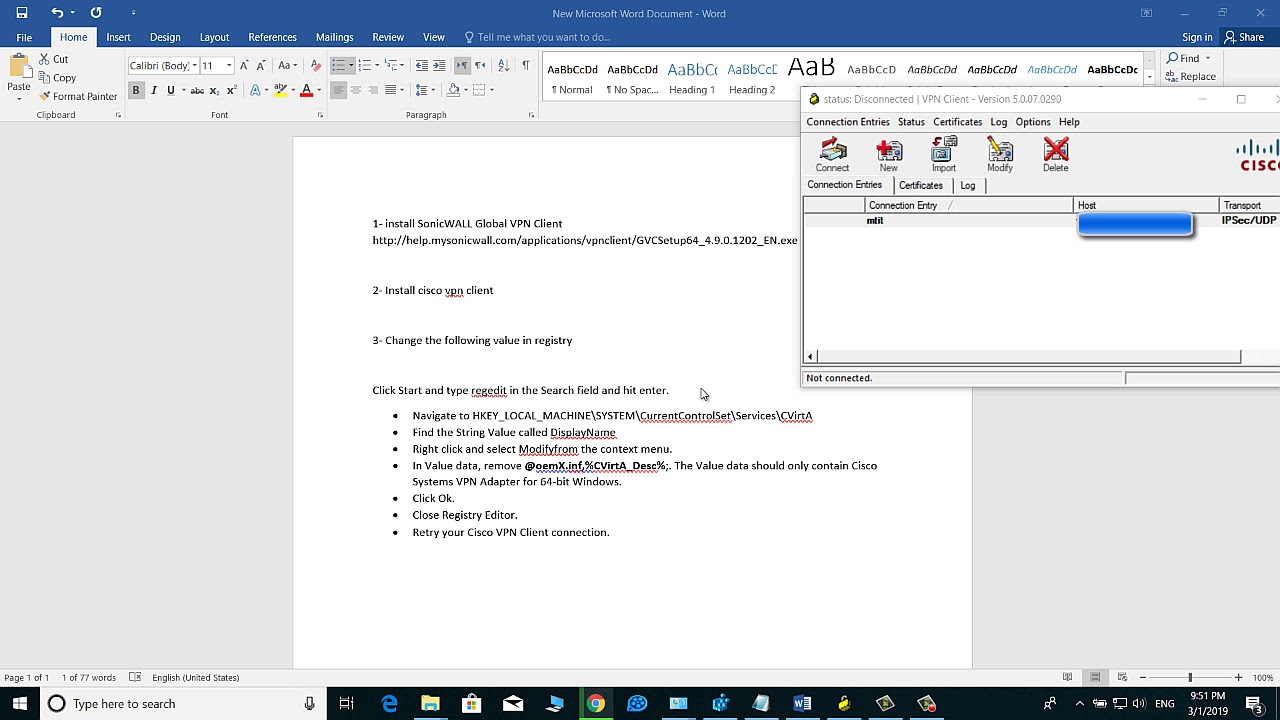
I'm a bit unclear about the PIX bit - the client has a log but it is
only populated on attempted connection. At the moment it only contains
this:
Cisco Systems VPN Client Version 4.6.00.0045
Copyright (C) 1998-2004 Cisco Systems, Inc. All Rights Reserved.
Client Type(s): Windows, WinNT
Running on: 5.1.2600 Service Pack 2
Config file directory: C:Program FilesCisco SystemsVPN Client

I can increase the logging of such things like IPSec, IKE, PPP, GUI
etc.
Thanks for all your help.
And yes 80.177.223.54 is the external NAT'd address of the firewall
(Cisco 857W).
The error: 'Secure VPN connection terminated locally by the Client. Reason 412: The remote peer is no longer responding' means the software VPN Client detected that the VPN server is not responding anymore and deleted the connection. This is caused by several different reasons, for example:
- The user is behind a firewall that is blocking ports UDP 4500/500 and/or ESP.
- The VPN client is using connecting on TCP and the default TCP port 10000 for NATT is blocked.
- The internet connection is not stable and some packets are not reaching the VPN concentrator/server or the replies from the server/concentrator aren’t getting to the client, hence the client thinks the server is no longer available.
- The VPN client is behind a NAT device and the VPN Server doesn’t have NAT-T enabled. In this case the user will not be able to send or receive traffic at all. It will be able to connect but that’s all. After some time the software client deletes the VPN tunnel.
Cisco Vpn Error 412
Solutions:
Cisco Vpn Client Error 412
- If you are using wireless, try to connect with cable
- Turn your firewall off, then test the connection to see whether the problem still occurs. If it doesn’t then you can turn your firewall back on, add exception rules for port 500, port 4500 and the ESP protocol in your firewall
- Turn on NAT-T/TCP in your profile ( remember to unblock port 10000 in your firewall)
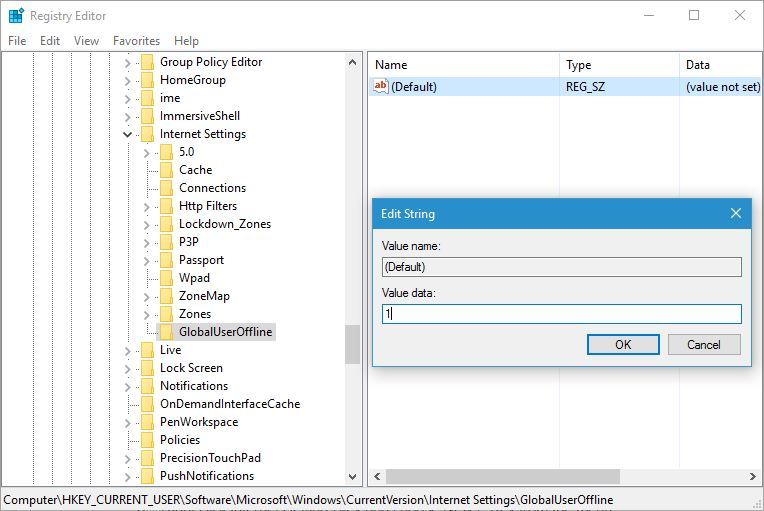
- Edit your profile with your editor and change ForceKeepAlive=0 to 1
